Recently, I was traveling with the train again and it so happened, that I was coming to Germany🇩🇪. It is not a secret, that things the train operators in neighbouring countries master effortlessly, seem to set a difficult challenge for the Deutsche Bahn (DB). To feed this statement with numbers: around 20 % of all trains in Germany were late in 2020 and that does not include the trains, that were cancelled for good or trains, that were less than 6 minutes late [1].
So it comes as no surprise, that I had problems connecting my Linux distribution workstation to the DB Wifi available on all ICEs[2].
$ cat /etc/os-release
PRETTY_NAME="Debian GNU/Linux 10 (buster)"
NAME="Debian GNU/Linux"
VERSION_ID="10"
VERSION="10 (buster)"
VERSION_CODENAME=buster
ID=debian
HOME_URL="https://www.debian.org/"
SUPPORT_URL="https://www.debian.org/support"
BUG_REPORT_URL="https://bugs.debian.org/"
And ofcourse I was not the first person in 2021 that complained, but apparently the DB did not put any measures in place. One problem is the poorely chosen IP addresses range, as people report [3] or [4].
The best (quickest) solution I came up with was to connect my Sailfish OS phone🐟 to the Wifi and use it as a Wifi adapter. Since Sailfish OS version 4.0.1.48 (Koli) does up to the best of my knowledge not support Wifi to USB tethering, I had to put in some work.
The trick was to setup a SOCKS5🧦 tunnel to the phone using USB as a physical layer. I am gonna start in laying out how I setup the connnection.
You fire up your terminal and type
$ ssh -D 5100 -C -N -q nemo@192.168.2.15
This forwards all traffic directed to 127.0.0.1:5100 to the phone, which has internet access over Wifi. Data can ofcourse also come back through that port. For more details about SOCKS and the command parameters checkout [5]. Mattias Geniar explains this much better than I ever could.
Sidenote:
SOCKS is definitely good for many things especially if you suspect a network, where your traffic is routed through, to have malicious susbscribers, trying to spy on you.
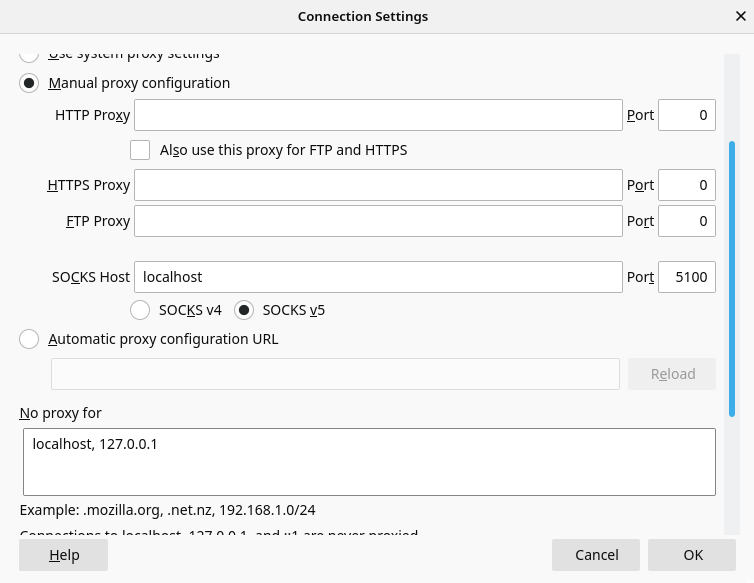
Next you need to tell your system or individual programs to route the data through the tunnel.
Firefox:
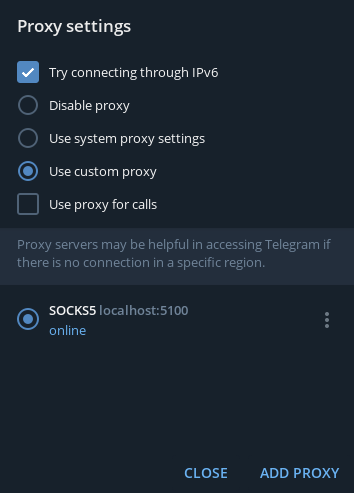
Telegram:
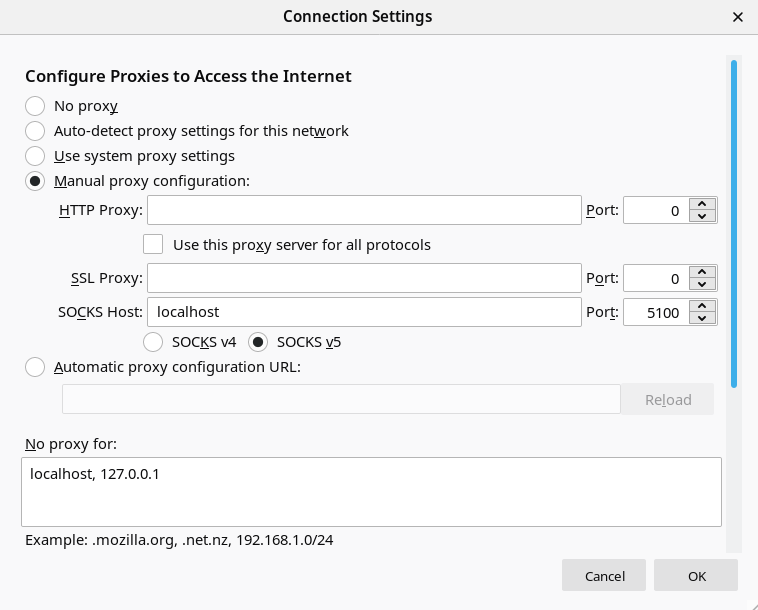
Thunderbird:
Optimally, your phone is connected to a VPN or your server using SOCKS as well, since you cannot really trust a public Wifi like that. Enjoy!
Bahn: Das sind die Strecken mit den meisten Verspätungen, ingenieur.de, 2021 ↩︎
WLAN im ICE und Intercity: So nutzen Sie WIFI@DB und WIFIonICE, 2021 ↩︎
Warum klappt Login im neuen WifionICE mit Ubuntu nicht mehr? ↩︎
Wie kann ich die WLAN-Anmeldeseite in der DB Lounge manuell eingeben, wenn si... ↩︎
Create a SOCKS proxy on a Linux server with SSH to bypass content filters ↩︎